“Someone has tried to access your Facebook account. Click here to change your password.”
We’ve all gotten this email or something similar for other accounts. Some of you may have even made the mistake of clicking the link and finding yourself on a page that asks you to login to continue. A few days later, you start noticing unusual activities from your profile: new followers, posts, likes, and comments. That most likely means a hacker got access to your login credentials, personal information, and perhaps even your ID.
Identity verification (IDV) has been around for hundreds of thousands of years. Today, IDV is used by businesses and governments to ensure that a user behind a process is who they claim to be and that they are not carrying out a process on another person's behalf or committing fraud.
In the past, IDV was mainly essential for financial services companies. However, today the value proposition for consumer apps and other online businesses is extremely powerful, especially due to ever-growing privacy requirements. With that in mind, let’s explore how IDV companies have tried to make online services safer and more trustworthy and where more can be done.
Overview of the IDV Market
The IDV market was valued at approximately $8 billion in 2020 and is predicted to double by 2025 with a CAGR of 14.8% by 2032 to reach a value of approximately $40 billion. COVID-19 accelerated the growth of the market by roughly 10 years, making IDV an important and widely used component in the process of enabling online interactions, whether monetary or otherwise.
Over the past few decades, the process of digitization in and across industries has seen an extraordinary hockey stick. With a little over five billion people online and more than 58% of customer interactions being digital, we find ourselves wrestling with the relationship between software and an individual's privacy.
The lack of control users have over their data, security, susceptibility to fraud, violation of privacy, compliance issues, and identity theft resulted in multiple serious incidents, such as data breaches from the likes of Cambridge Analytica and Facebook. Today the public’s awareness and understanding of data privacy and online safety is ever growing, putting the pressure on online businesses to provide safer and more reliable services.
Errors & Trust: Pain points in the IDV Market
Across various industries, businesses tried to own the IDV processes. For example, banks and airports have physical ID scanners and a human to validate one’s identity––a process that requires the customer to be there physically during opening times and wait in long queues. Online businesses, such as Transferwise, Airbnb, Uber, Coinbase, Dapper Labs, and many more have teams of 100-plus individuals to focus on ”Know Your Customer” (KYC), onboarding, and to limit the creation of duplicate accounts.
This process is extremely fragmented, leaving room for many errors and can cause lengthy delays to be verified, like Coinbase with their six-week wait time. More recently, these businesses tried to augment these functions with third-party providers. However, the pain points remain in addition to fraudsters still getting access and users struggling to get verified.
In most industries, users with fake identities really only impact the business. But when trust is broken on dating and social platforms, it harms users and society at large. And the financial, psychological—and sometimes physical—impact on a person is real. It is, however, also important to acknowledge that the inefficiencies associated with trying to solve these issues often drive consumers to churn and find alternative service providers.
IDV can easily be compared with payments. They are both complex to build and require integrations to various disparate APIs and third-party data providers. This means that building something so complex is not likely the core competency of the companies that require IDV. This leaves the door open for third-party companies to build IDV tech and provide it as a service.
Market Opportunity within the Identity Verification Stack
There is huge demand for IDV solutions that provide frictionless authentication, simplicity, and ease of integration to reduce fraud, the risk of data breaches, and effortlessly comply with privacy regulations. The IDV market is broken up into multiple, fast-growing segments that offer partial solutions to cover all services related to “digital identity.”
Below are the key areas that we’ve identified that make up the Identity Verification stack.
So here we go:
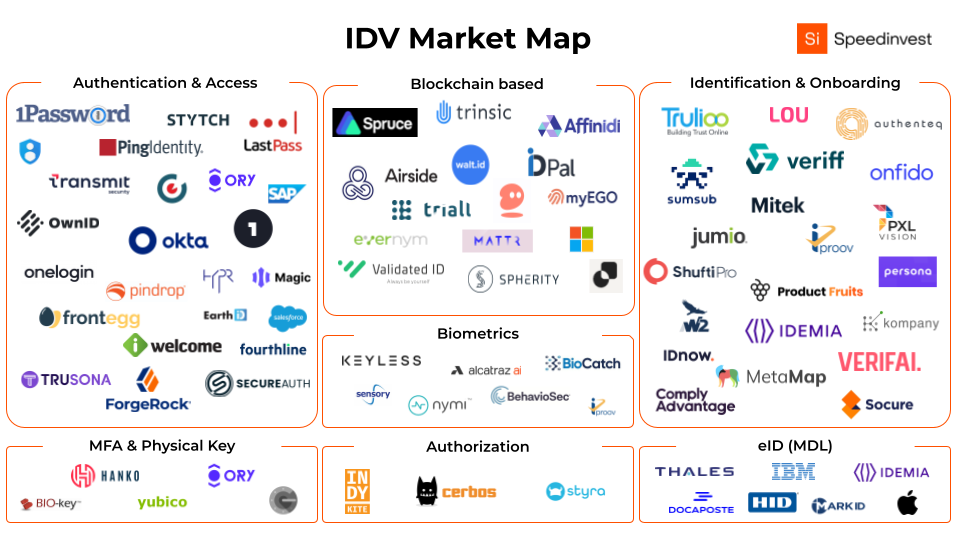
Authentication (AuthN): login - access
AuthN is about knowing who you are interacting with online. In other words, identifying individuals. Within this vertical there are quite a few successful players that are built to solve for the services of AuthN. These include the likes of Okta ($16 billion), Ping Identity ($2 billion), and ForgeRock ($2 billion). Those companies were primarily built around the bane of the internet––the username and password. The username and password model is broken. It’s insecure and provides a now outdated user experience.
The future of AuthN is passwordless. The passwordless space is looking to replace the overall identity stack highlighted above. Hence why we didn’t create its own layer. Some of these players include Transmit Security or Stytch (raised $126.3 million to date). On the other hand, other players within the authentication space, such as OwnID, are trying to redistribute the identity management into the hands of the consumers. Both approaches have significant potential and it’s likely that in the coming months and years there will be a few more unicorns sprouting from the next generation of companies building within the passwordless authentication space.
New approaches will allow for complete self-service by employees, customers, and the administrators that manage their accounts. We’re already seeing some of the next generation of companies working in this area, such as WorkOS and FrontEgg.
Multi-Factor Authentication (MFA)
MFA solutions require the user to provide two or more verification methods, such as a hardware, one-time passcode (OTP) and/or biometrics to gain access to a resource, like an application, online account, or VPN. MFA is much safer than just asking for a username and password, which reduces the likelihood of cyber attacks.
Until recently, MFA remained somewhat inconvenient. Think about those times you tried to log into an account tied to an old phone number and couldn’t access the OTP pin. Gaining access to the account was a nightmare.
Now, Apple, Google, and Amazon have started rolling out support for Passkeys, namely Fast Identity Only 2 (FIDO2) authentification. FIDO2 is an unphishable, standards-based passwordless authentication method that can come in any form factor through the use of security keys. Keys are much more secure than passwords since the keys cannot leave the enrolled devices and are stored in the secure enclave.
The best example here are Apple devices when unlocked with TouchID or FaceID. Although the process feels like just one authentication process when using the TouchID or FaceID function, it’s actually a two-factor authentication. Hanko is a notable player in the space, which allows easy implementation of FIDO2.
Biometrics
The days of using your PIN every time you make a payment or unlock your phone might soon become a thing of the past. Apple’s FaceID was a huge step forward in the development of Biometrics. Due to its unique identifier attributes, Biometrics often come into play as part of two-factor authentication (2FA) and MFA for business use cases. Moreover, they enable a seamless onboarding process and provide a much better user experience. Some notable players in the space include alcatraz ai, Veriff, and Stytch.
Based on that, what does the future of biometrics look like? As can be expected, the technology isn’t flawless. Recently, many issues around bias, privacy, and security have come up resulting in an increase of new legislation on privacy, which companies are NOW actively working towards complying.
Although facial and fingerprint recognition is far more advanced today than it ever was before, much more can be done with the technology with regards to decreasing the risk of duplication, and making the tech better e.g. 3D with scanning and securing the biometric databases. Moreover, the scope of use cases for biometrics is increasing––with companies like Ceritfic––by providing biometric identity verification for medical procedures.
Identity proofing and onboarding (KYC/KYB)
While authN is often a precondition for granting access to applications, solutions in this category are not about managing a user’s access. The KYC/KYB category is mainly about risk assessments that require information beyond core identity attributes. It’s about identifying with whom you are interacting.
KYC/KYB solutions enable background checks in a data-centric approach. Companies in this space tend to be positioned as middlemen who get user data from their customers and verify by comparing it with static data from many different data sources, like governmental databases. Some notable players in the space include Onfido, Veriff, and Jumio.
The main use cases for these are:
- Regulatory requirements (e.g. require users to confirm they are of legal age)
- Rising standards and user expectations for digital interactions (e.g. Uber, Airbnb, and when lending assets)
- Brand and fraud protection (e.g. prevention of association with fraudsters)
Contemporary IDV services leverage machine learning and automation to provide instant verifications without human involvement. This dramatically improves customer experience, overall costs, and enables a whole set of new use cases. This is also replacing some of the traditional identity proofing mechanisms, like the Knowledge Based Authentication (KBA) or database checks that can be inconvenient and inaccurate. Some of the next generation companies in this area include Persona and Berbix.
Authorization (AuthZ) or Access Control: User permission
Authorization is the process of validating what an authenticated user can access. In our opinion, AuthZ is the most underserved and complex segment of the IDV stack. In simple terms, upon verification of a user identity, the user then gets granted specific “access rights” to specific data via access control list (ACL). The specificity of these access rights can vary widely, going from the “superusers” that have access to the entire data repository to the user only having read access to a specific data row.
Now, let’s imagine that a bank accidentally gives its clients “Superuser” access. That would be a security catastrophe. The user would be able to read and amend their personal and other client data, hence the importance for AuthZ to be done right.
Some notable players in the space include Cerbos, Styra, and our very own Indykite (formerly founder at ForgeRock). These players are often third party to AuthNs like Okta, WorkOS, and Magic. We strongly believe that there is still a lot to be built in the space.
eID - Management of users and access
The players in this space tend to target governments and tenders with more than 5,000 employees to guarantee secure daily interactions. Trusted digital identities are essential for digital transformation. As business growth depends on these digital services, organizations need trusted identities to support rapid development and reduce fraud. These include the likes of Thales, IBM, Apple, HID, and more on the market map above.
The Future of Identity: IDV and Crypto/Web3
I know what you’re thinking right now. Oh, no… Not another investor trying to integrate Web3 into another category.
But hear me out! IDV is just as important in Web3 as it is in any other industry––starting from the simple idea of moving away from Social Login (i.e. using Facebook to login to ‘random app’) and moving towards self sovereign identities (SSIs) powered by your crypto/identity wallet.
By decentralizing the entire IDV stack as opposed to centralizing on the big tech platforms, web3 IDV solutions, such as Spruce or our very own walt.id, provide people or organizations with the autonomy and control over their identity. This is known as self-sovereign identity (SSI). All businesses and individuals have a unique set of identifying information. This information can include a birth certificate, medical information, university degree, driver license, incorporation document the list goes on.
In the physical world, these come under the form of card or paper documents stored somewhere safe, such as your wallet or a safety deposit box. When the identity holder needs to present their identity documentation (say you want to open a bank account)––instead of bending over backwards to provide all of the necessary documents to prove your identity, you can simply show your digital identity (ID) and authenticate yourself in a matter of seconds.
A growing demand for simple IDV solutions
Another appealing aspect of SSIs is that as the identity holder, you have full control over what part of your identity to share. Oftentimes, the entities requiring identity documentation receive more information than is required. With SSI, you can directly control what information to share and what not to share. But we’ll dive deeper into this topic in the near future. Keep an eye out for it!
There is an ever-growing demand for IDV solutions that provide simplicity and ease of integration to reduce fraud, reduce the risk of data breaches, and effortlessly comply with privacy regulations. While online fraud is accelerating alongside regulatory requirements, more and more digital products are moving away from passwords. In time, the identity stack will move up a curve of user focus and feature focus. The user focus will move from just IT to developers, employees and customers, while the feature focus will move from just security to customer experience, first-party data, privacy, and Web3.
We will continue closely looking at this constantly evolving space. And if you like solving technical problems, want to accelerate technological progress, and are thinking about working on an IDV solution, we’d love to hear from you!